Develop an ISMS compliant to ISO 27001
Oriel STAT A MATRIX has successfully assisted thousands of organizations in attaining certification to ISO 9000 and related ISO standards like ISO 27001 using our 14-step process.
The Program:
-
Focuses on increasing organizational effectiveness and efficiency.
-
Yields a framework that ensures process consistency and optimal results going forward.
-
Transfers knowledge and skills through coaching, mentoring, and training, thus ensuring that your organization remains successful after we leave.
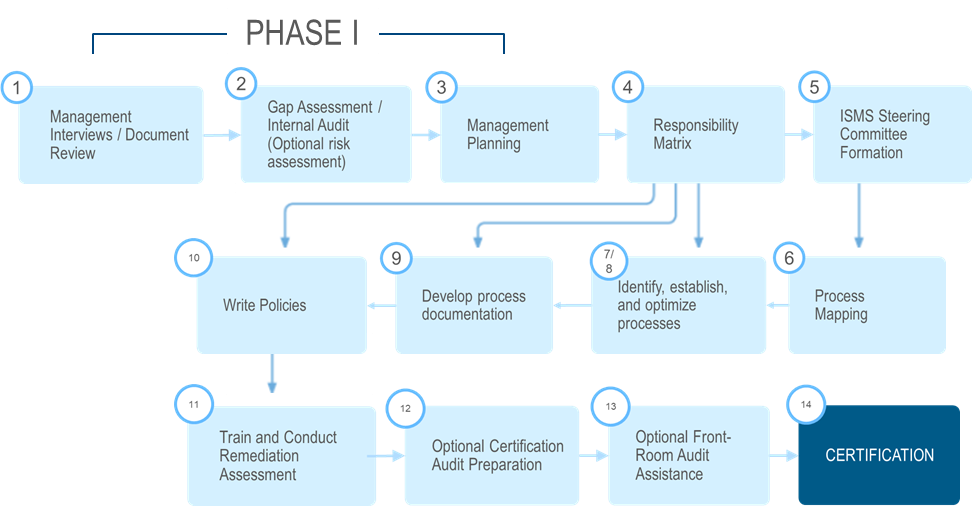
Phase I (Steps 1 – 3)
If you already have a limited ISMS in place, we will first assess your current level of ISMS compliance. This process will uncover opportunities for improvement and yield the information needed to make an informed assessment of the amount of time and resources required to comply with ISMS. From here we will provide a detailed roadmap that will be used to prepare for your initial ISO 27001 certification audit.
An optional Risk Assessment to ISO/IEC 27005 can be conducted during Phase I. The cornerstone of the ISMS is an information security risk assessment. For clients have not completed one, this service can be integrated into the ISMS development process.
Phase 1 provides an understanding of:
-
Your current level of compliance
-
Where in the organization there are opportunities for improvement
-
The required path to move forward towards certification
-
The amount of time and resources required to move forward with certification
Phase II (Steps 4 – 14)
During the second phase of the program we will develop an action plan for you that will take you all the way to the point where you will be ready for your ISO 27001 certification audit.
A key step in this Phase is Policy Development. During this step we provide a customized policy stack that can be implemented to achieve ISO 27001 certification.
Typical Policies include:
-
Information Security Policy (For Employees)
-
ISMS Policy/Charter (Program establishment)
-
ISMS scoping document
-
ISMS/Risk Committee Charter
-
ISMS Risk Assessment Plan/Procedure
-
Mobile Device/Telework Policy
-
Human Resources Security Policy
-
Asset Management & Disposal Policy
-
Acceptable Use Agreement
-
Information Classification
-
Access Control Policy
-
Cryptography Policy
-
Physical Security Policy
-
IT Security Policy
-
Third Party & Supplier Security Policy
-
Incident Response Plan/Procedure
-
Business Continuity / Disaster Recovery Plan
ISO 27001 Training
-
ISO 27001 Executive Management Training: What does ISO 27001 certification entail?
-
ISO 27001 Overview Training: Understand New and Revised Process so that your organization can maintain compliance and ensuring successful surveillance outcomes
-
ISO 27001 Audit Best Practices